Azure Policy - Subnets should have an Network Security Group
I often find it useful to create a proof for a security control and demonstrate how it works and pick up some useful techniques on the way. Download the Postman export here. The issue with this fine policy is in the way the latest Terraform works. It creates the subnet prior to associating the NSG which means it is blocked from creating the subnet. Use the Terraform in the initial_env directory to create the starting point for the lab work.
Attach the Policy to the Resource Group
Obtain the 'Subnets should have a Network Security Group' policy definition from here and add to your subscription. The name may conflict with a built-in policy so add something to the end - I added Andy on the end to differentiate it.
Attach the policy to a resource group. In this example the resource group 'az-900'.
 |
| Azure Policy Definition |
Assigned to the Resource Group az-900
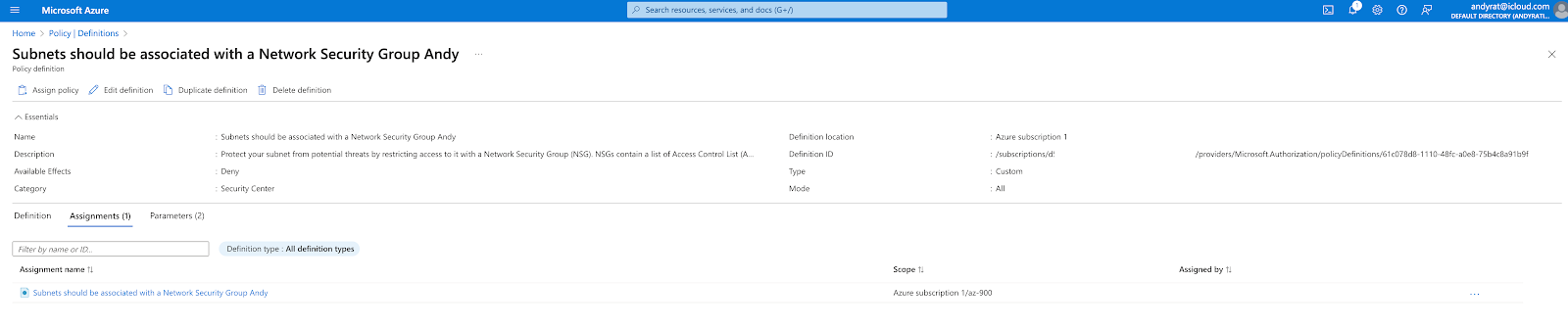 |
| Azure Policy Assignment |
Postman Create Subnet
Use the HTTP API to create a subnet and associate an NSG in a single step.
Using Try It:
First get the Subscription ID.
Outputs the Subscription ID.
Next, create a service principal (SP).
This provides the necessary credentials for use in postman.
Create a new Collection in Postman called Azure API.
From the right-hand side Postman toolbar select Environment and click add.
 |
| Add Environment variables |
At the Environment level add a variable for the Tenant ID. This is used in the get-token request.
This can be obtained by using this command:
Create Environment variables in Postman with the values as shown below as shown and click save.
| Variable Name | Output Label |
| ClientID = | AppID |
| tenantID = | tenant |
| clientSecret = | Password |
| resource = | https://management.azure.com/ |
| resourceGroup = | [Resource Group] |
| subscriptionID = | [Subscription ID] |
| bearerToken = | "leave it blank, we will programmatically fill the field later" |
| test_number = | 1 |
Environment Variables in Postman.
 |
| Environment Variables |
Set the Authorisation method in the Azure API Collection.
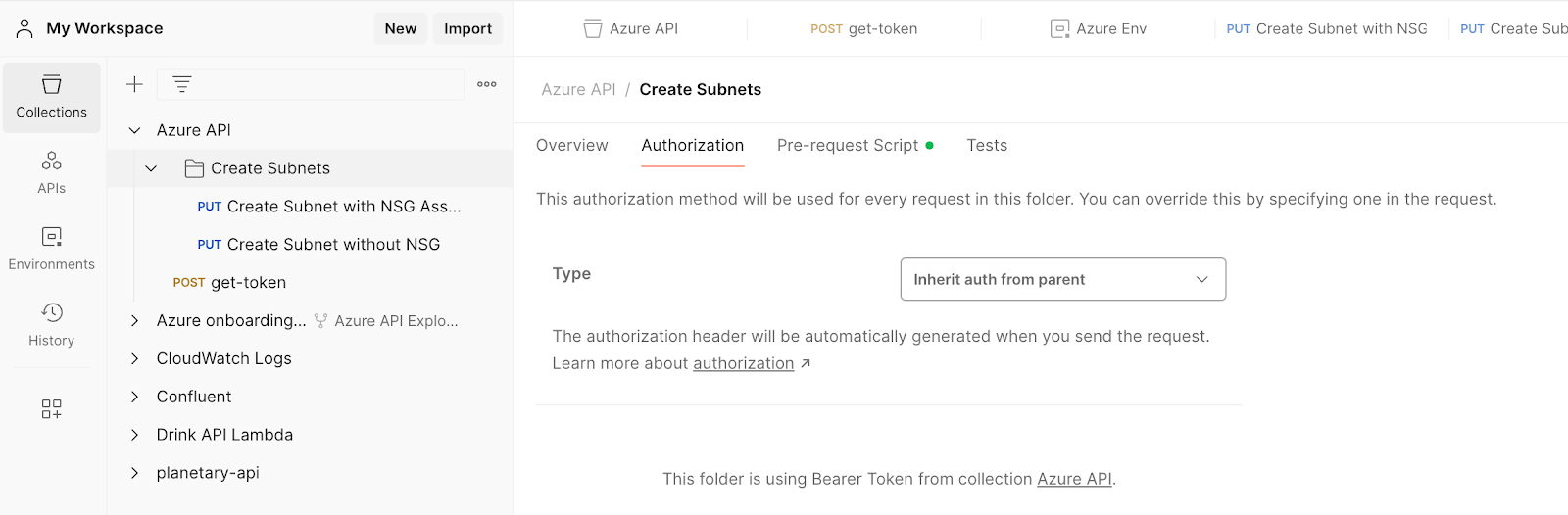 |
| Inherit from parent |
Create a new post request called get-token to the oauth endpoint:
with the form as shown below:
Add a test in the tests tab store the bearer token to an environment variable called bearerToken that will be sent with all requests.
In Postman select the Tests tab and paste the JavaScript in.
 |
| Get-Token JS to store bearer token |
For this request the Authorisation method should be left set to No Auth, as this will be used to obtain the bearer token.
 |
Create Folder in the Azure API Collection called Create Subnets
Add this short script to increment an Environment variable called test_number under pre-request script.
Create a new PUT request under the folder called 'Create Subnet without NSG'.
Create a JSON body for the request (ensure the AddressPrefix aligns with the VNET, in this case the VNET vent1 10.0.0.0/16). Each test will increment the value of test_number.
It should look like this in Postman
Create a second request by duplicating the first, and rename it in to 'Create Subnet with NSG Associated in existing VNET' with a JSON body as shown.
Make sure the NSG you want to associate with has already been created.
Run Tests:
That's it, just run the get-token request and then the two tests:
- Create Subnet without NSG
- Create Subnet with NSG Associated the existing VNET vent1
Results:
- Fails with a "403 Forbidden" error code. Disallowed by Policy with the message set in the policy.
- Success with "201 Created" response code.
Clean-up
This will delete ALL of the subnets in the resource group VNET used (change names as needed).
Terraform
In this post I looked at how the Azure Policy prevents the creation of a subnet without an associated Network Security Group. I have created two Terraform scripts showing terraform for the first test this script will fail with Policy effect set to Deny. The second script creates another resource group and assigns the same policy but with it set Audit only which works as Terraform can create the subnet without being blocked.











Comments
Post a Comment