Modern Honey Network - Extract Threat Intel
The Modern Honey Network is an application for the deploying and collecting data from Honey Pots. Honey Pots can be a very useful detective control but they can also be useful for collecting threat intelligence.
There is great introductory blog post on Lenny Zeltser’s blog. I use a popular cloud service to deploy my honeypots on the Internet.
I use it collect various Threat Intelligence such as scanning IPs and source addresses that are doing password brute force attacks. I feed the IP addresses into tools like Security Onion and SOF-ELK.
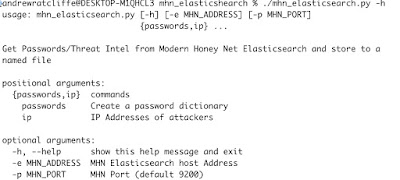
As MHN can write to Elasticsearch via logstash installed locally it’s easy to query and extract the data from there. I wrote a small python program to extract either unique IP Addresses or a unique password list that can be used for checking passwords against to make sure you don’t use ones that appear in the attackers dictionaries.
Once extracted, the unique IP addresses can be used as threat intelligence in your SIEM or you could further process them to ranges and create Snort or Suricata rules in Security Onion.
The passwords can be used as a dictionary for penetration testing.
This just scratches the surface of the potential use cases for honeypot data.


Comments
Post a Comment